In this blog we will see how to Exempt MFA additional security for the users from Corporate network and using ADFS Claim Rules.
What is MFA ?
Multi-factor authentication (MFA) is a method of authentication that requires the use of more than one verification method and adds a second layer of security to user sign-ins and transactions
IP Whitelist allows administrators to add an extra level of security and convenience by only requiring users to perform MFA when accessing resources from outside their corporate network. This can be done two ways:
Whitelisting of IP addresses: White-listing of IP Address in Azure portal.
Configuring claim rules in AD FS: Configure ADFS Claim rules to Exempt MFA from Corporate Network
Whitelisting of IP addresses
Login in to https://manage.windowsazure.com
Select Active Directory in the below screen.
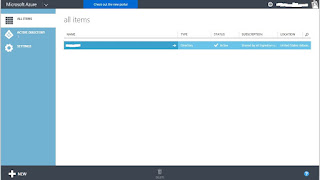
Once you select Active Directory search for Office and select Exchange from the below screen.
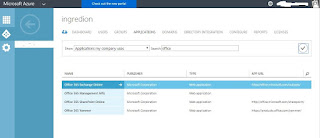
Select Configure in the Below screen.
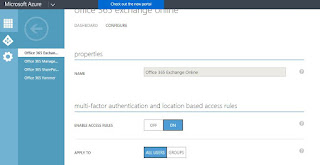
Enable Access Rules : ON
Apply to : Depending up on your requirement select All users/Groups
Rules : Requires MFA when not at work. it will only prompt MFA when users try to access from outside the corporate network.
Rules : Under rules select "click here to define/edit your work network location. it will redirect to other page you have to list out all the Public IP Address of you work Network.
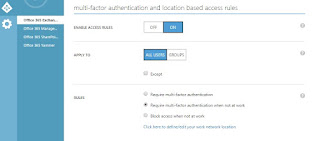
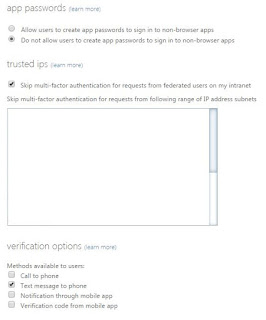
in the below screen under trusted IP's enter all the required IP's to Exempt user for MFA and click Save.
It might take 24 hours to Propagate in all the O365 servers.
ADFS Claim Rules to Exempt MFA
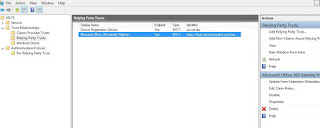
Open ADFS configuration Manager, Click on Edit Claim rules and create new claim rule.
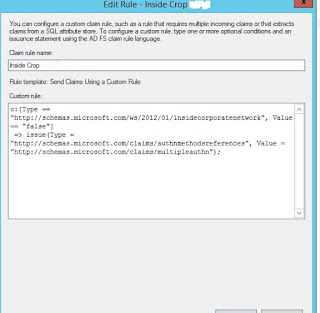
Below is the Claim Rule
Hope this helps!!!!
What is MFA ?
Multi-factor authentication (MFA) is a method of authentication that requires the use of more than one verification method and adds a second layer of security to user sign-ins and transactions
IP Whitelist allows administrators to add an extra level of security and convenience by only requiring users to perform MFA when accessing resources from outside their corporate network. This can be done two ways:
Whitelisting of IP addresses: White-listing of IP Address in Azure portal.
Configuring claim rules in AD FS: Configure ADFS Claim rules to Exempt MFA from Corporate Network
Whitelisting of IP addresses
Login in to https://manage.windowsazure.com
Select Active Directory in the below screen.

Once you select Active Directory search for Office and select Exchange from the below screen.

Select Configure in the Below screen.

Enable Access Rules : ON
Apply to : Depending up on your requirement select All users/Groups
Rules : Requires MFA when not at work. it will only prompt MFA when users try to access from outside the corporate network.
Rules : Under rules select "click here to define/edit your work network location. it will redirect to other page you have to list out all the Public IP Address of you work Network.

in the below screen under trusted IP's enter all the required IP's to Exempt user for MFA and click Save.

It might take 24 hours to Propagate in all the O365 servers.
ADFS Claim Rules to Exempt MFA
Open ADFS configuration Manager, Click on Edit Claim rules and create new claim rule.


Below is the Claim Rule
=> issue(Type = "http://schemas.microsoft.com/claims/authnmethodsreferences",
Value = "http://schemas.microsoft.com/claims/multipleauthn");"
Hope this helps!!!!
No comments:
Post a Comment